 |
| Image source: Article |
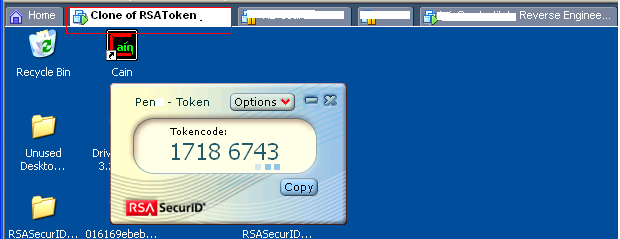
Are you blindly trusting your RSA tokens? Read the article to find out. Or are you using GuardTime keyless signatures to prove they have not been compromised?
A site dedicated to providing credit unions with relevant news and information related to security and information technology.
 |
| Image source: Article |
No comments:
Post a Comment