Wednesday, December 30, 2009
Things That Have Gone Away: Remember These?
Adjusting Horizontal And Vertical Holds on a TV
Be Kind-Rewind video tapes
Calling A Phone Sex Line
Calling Collect On A Payphone
Cash Register Used Manually Entering The Prices (rather than scanning them)
Changing The Ribbon On A Typewriter
Converting Your Albums From Vinyl To Cassette Tape
Cuff Links
Dialing A Rotary Phone
Filing Cards In A Library Card Catalog
Finding Channels On UHF
Getting Off The Couch To Change Channels On Your TV Set
Having Your Gas Pumped For You And Your Oil Checked At A Full-service Gas Station
Kick Starting A Motorcycle
Knowing What Part Of Town Someone Lives In By Their Phone Exchange
Loading A Reel To Reel Tape Drive
Making An Operator Assisted Phone Call
Making Hot Chocolate By Heating Milk in a Pan, Then Adding Cocoa Powder and Sugar (remember the "skin" on the milk?)
Meeting People By Answering Personal Ads In A Newspaper Or Magazine
Opening A Can Of Beer Or Soda With A Church Key
Peeling The Developer Layer Off A Polaroid
Percolating Coffee
Placing A Coin On A Tone arm To Prevent Skipping
Popping Corn In A Pot With Oil
Porn Not From The Internet
Putting A Needle On A Vinyl Record
Rewinding An Audio Cassette Using A Bic Pen
Selling Something In The Classified Ads
Shave With A Straight Razor
Shorthand
Smelling A Freshly Mimeographed Test Paper
Switching To High Beams By Stomping On A Button In The Floor
Taking The Tape Out Of An Answering Machine
Testing TV Tubes At the Drugstore
Using Carbon Paper To Make Copies
Using Correction Fluid
Using A Party-line Telephone
Using A Pay Toilet
Gadgets of the Decade
2001: The iPod
2002: The Dyson DC07 Vacuum Cleaner
2003: The Mainstream DVR
2004: The Motorola RAZR Cell Phone
2005: Personal GPS Navigation Devices
2006: Intel-Powered Macbooks
2007: Tie - the iPhone, the Wii, and the Flip camera
2008: Netbooks
2009: Explosion of e-readers
See the entire list and read the details at: http://www.fastcompany.com/pics/gadgets-decade
Tuesday, December 29, 2009
December News & Views Published Below
CU SECURITY & TECHNOLOGY News - Providing a brief summary of news and information related to security and technology issues for credit unions - Plus some interesting and fun web sites . . .
Monday, December 28, 2009
Five technology trends to watch in 2010
5: The consumerization of IT - This is something we’ve been talking about for a couple years but the trend is accelerating. We see it in employees using their own personal laptops and devices for work tasks and using freely available Web tools to help them get their jobs done. This can create a whole host of problems for IT, but in most cases you don’t want to squash it altogether. What you’ll need is a policy that gives employees guidance on how and when these types of tools can and can’t be used, and why.
4: Desktop virtualization - TechRepublic recently asked its CIO Jury about desktop virtualization and 75% said they weren’t interested. However, the 25% that ARE interested are very enthusiastic about using it to cut costs and simplify IT support. In 2010, it’s going to interesting to see if this trend gains momentum and becomes more mainstream, or if it’s simply relegated to a few niche scenarios and industries.
3: E-readers - While most of the buzz around e-readers is centered around consumers readings books and newspapers, there are also a new set of e-readers that will hit the market in 2010 that are aimed at helping businesses streamline the meetings that require huge stacks of paper and bring more multimedia capabilities to business documents. For more ammunition on why you should follow this trend, see Jack Wallen’s article “10 reasons why e-readers make sense in the enterprise.”
2: WAN acceleration - I consider WAN acceleration to be one of the best kept secrets in the IT and business worlds. By caching big files and often-used documents, WAN acceleration appliances and software can save big money on bandwidth costs and give your branch offices and remote workers far better performance on their business applications. Companies like Riverbed are even taking WAN acceleration a step further and using it to help speed up hosted cloud applications by partnering with major SaaS providers. All of this makes WAN acceleration one of the hottest projects in IT right now, because it can offer fast ROI and immediate productivity benefits.
1: Berries, apples, and robots - What do these three things have in common? Well, of course, we’re talking about smartphones with BlackBerry, Apple iPhone, and Google Android. These are the three smartphone platforms that have the most momentum heading into 2010. With smartphones becoming standard tools for more and more business workers, it’s going to be important to watch which devices users gravitate toward, which platforms offer IT more security and manageability features, and which ones developers latch on to as the best place to build new applications for business users.
http://blogs.techrepublic.com.com/hiner/?p=3473&tag=nl.e101
Thursday, December 24, 2009
FBI: 19,000 Matches to Terrorist Screening List in 2009
The watchlist, which includes approximately 400,000 individuals, is used to screen visa applicants, gun buyers and suspects stopped by police and to stop some air travelers for extra screening or interrogation.
http://www.wired.com/threatlevel/2009/12/terrorist-watchlist
Wednesday, December 16, 2009
A Job Even Better Than Working At a Credit Union
Outside England 's Bristol Zoo there is a parking lot for 150 cars and 8 buses. For 25 years, its parking fees were managed by a very pleasant attendant. The fees were £1 for cars ($1.40), £5 for busses (about $7).
Then, one day, after 25 solid years of never missing a day of work, he just didn't show up; so the Zoo Management called the City Council and asked it to send them another parking agent. The Council did some research and replied that the parking lot was the Zoo's own responsibility. The Zoo advised the Council that the attendant was a City employee.
The City Council responded that the lot attendant had never been on the City payrole.
Meanwhile, sitting in his villa somewhere on the coast of Spain (or some such scenario), is a man who'd apparently had a ticket machine installed completely on his own; and then had simply begun to show up every day, commencing to collect and keep the parking fees, estimated at about $560 per day -- for 25 years. Assuming 7 days a week, this amounts to just over
$7 million dollars!
And no one even knows his name.
Tuesday, December 15, 2009
Six cyber trends outlined by I.D. theft center
The report is based on developments during the past year and notes what's ahead in 2010, including trends in criminal activity and law enforcement.
The report also outlined six trends ITAC anticipates for 2010:
1) More criminals will use malware to steal usernames and passwords, and recruit accomplices as "money mules" to open phony accounts and transfer funds. "It is the responsibility of consumers and businesses alike to demand the best security protection and to implement it into their everyday experiences," said Michael Stanfield, CEO, Intersections Inc., a CUNA Strategic Service.
2) More collaboration on cyber security. The Obama administration will continue to break down silos within the government and collaborate more with the industry as it develops and implement cyber security policy, ITAC said.
3) Expanded use of identity management solutions to address identity theft, data breaches and cybercrime.
4) Changes resulting from "Red Flag" rules. Red flags are any activity or practice that indicates possible identity theft. Consumers will face questions about address changes and other behavior, including missed payments or changes in spending patterns. Consumers may be annoyed until they adjust to the new levels of scrutiny.
5) Stiffer sentences for those convicted of identity theft. The law requires a mandatory two-year sentence for aggravated identity theft. Prosecutors also are pursuing added jail time for related felonies, including wire fraud and use of unauthorized access devices.
6) Possible federal regulation of breaches of consumer data. The Senate is slated to consider two measures that would regulate how public and private organizations protect personal information.
Counterfeit credit/debit card fraud: Let's stop it now
 > Stare: It’s no longer considered rude to stare at your card for the entire time it’s in the hands of a clerk or waiter.
> Stare: It’s no longer considered rude to stare at your card for the entire time it’s in the hands of a clerk or waiter. > Change: The bad guys have figured out the number-increment algorithm many banks use. If at all possible, make sure the last eight digits of the new credit/debit card’s number are different.
> Check: The average time between stealing credit card information and using it on-line has dropped from 10 days to three. It is recommended that you check your on-line accounts at least that often.
Mr. Patterson’s endeavor
Those tips are important. Yet, they are overshadowed by Mr. Patterson’s real quest. Here is what he wants to do:
“Completely eradicate counterfeit card fraud world-wide in the next 24 months. With the banks losing over 4 billion dollars a year and growing rapidly, the industry is ready to fight back. Organized crime has declared this fight, and it will take a unified effort to repel.”
We all know about credit/debit card fraud. What surprised me was the scope of counterfeit card fraud. Expert after expert pointed out that using counterfeit cards or information obtained from credit/debit cards supports most illegal activity throughout the world.
Counterfeit cards
This YouTube video will give you an idea of how simple it is to steal information embedded in a credit/debit card’s magnetic strip. As the video shows, the only hardware required is a computer, card reader, and magnetic strip card writer. One expert commented on how easy it is to buy card skimmers (readers) on eBay. So, I looked and, sure enough (courtesy of eBay):
(Read the rest of the story at: http://blogs.techrepublic.com.com/security/?p=2825&tag=nl.e036
Monday, December 14, 2009
The Google Phone: Risks, rewards and wild cards
 It didn’t take long for pictures of this Google phone to hit Twitter. The Wall Street Journal then followed up with a few more tidbits.
It didn’t take long for pictures of this Google phone to hit Twitter. The Wall Street Journal then followed up with a few more tidbits. > Google’s Nexus One will up the ante vs. Apple;
> HTC will make the device;
> The device won’t be tethered to any carrier and Google will sell it online;
> Google wanted to control the hardware, software and user experience completely.
So what is Google up to with Nexus One? The answers are a little fuzzy, but here’s a crack at Google’s calculus behind launching a phone that could alienate partners, drive wireless innovation and alter the competitive landscape among other things.
Read more about the Google phone at: http://blogs.zdnet.com/BTL/?p=28432&tag=nl.e539
Friday, December 11, 2009
How Fake Sites Trick Search Engines to Hit the Top
Security researcher Jim Stickley displays logs on his laptop from Internet scams he created for a...
Security researcher Jim Stickley displays logs on his laptop from Internet scams he created for a study for a California financial institution at his home in La Mesa, Calif., Monday Dec. 7, 2009. Stickley's study showed some of the most trusted Internet search engines gave high ratings to fraudulent web sites. (AP Photo/Lenny Ignelzi)
(AP)With a little sleight of hand, con artists can dupe them into giving top billing to fraudulent Web sites that prey on consumers, making unwitting accomplices of companies such as Google, Yahoo and Microsoft.
Online charlatans typically try to lure people into giving away their personal or financial information by posing as legitimate companies in "phishing" e-mails or through messages in forums such as Twitter and Facebook. But a new study by security researcher Jim Stickley shows how search engines also can turn into funnels for shady schemes.
Stickley created a Web site purporting to belong to the Credit Union of Southern California, a real business that agreed to be part of the experiment. He then used his knowledge of how search engines rank Web sites to achieve something that shocked him: His phony site got a No. 2 ranking on Yahoo Inc.'s search engine and landed in the top slot on Microsoft Corp.'s Bing, ahead of even the credit union's real site.
Read the rest of this story at: http://abcnews.go.com/Technology/wireStory?id=9282914
Thursday, December 10, 2009
From a Security Perspective, Can You Really Identify The Bad Guy
Wednesday, December 9, 2009
Sunday, December 6, 2009
Credit Union Retired Executives (CURE) Online Advisory Service Launched
We are pleased to announce the debut of its unique online advisory service — CURE, at www.CURetiredExecs.com — a secure, virtual network of retired credit union executives who are volunteering their time and expertise to support those working today on the front lines of the credit union industry. The first of its kind, this new website is the only place to go 24/7 for confidential advice — free of charge, thanks to the website’s Supporters — about the many operational issues facing credit unions today.
Holly Herman, Executive Director, stated, “Experience matters! We’ve assembled an incredible team of Advisors, retired credit union executives with an unmatched depth and breadth of experience — experience that has gone largely untapped until now. We also have an exceptional group of Supporters from around the industry, who are making it all possible.”
Getting started is easy. Visit www.CURetiredExecs.com, register, and ask your first question. Visitors have their choice of advisors with expertise in a wide variety of areas, and are assured total confidentiality — and a customized answer within 3 business days, offering suggested solutions, recommended alternatives, and new perspectives on the question at hand.
Herman added, “In these especially difficult times for all of us, we’re confident that this service will prove invaluable in tackling and overcoming the challenges of the day, to ensure that credit unions everywhere can continue to offer the best in financial services to their members.”
CURE is a resource for credit union professionals to ask questions and to use as a sounding board. It's the number one place to go for advice on anything relating to your credit union. CURE connects credit union professionals with the nation's finest credit union retired executives for free and confidential advice. We have advisors waiting to share their experience and opinions with you. Visit http://www.curetiredexecs.com/ to get started.
Thursday, December 3, 2009
Scam Wave Hits CUs in Several States
 Two scams circulating in Northern Colorado involve texting to cell phones of members and nonmembers. The messages invoke the name of a defunct credit union, Norlarco CU, which was acquired by Public Service CU in Denver (Coloradoan.com Dec. 1).
Two scams circulating in Northern Colorado involve texting to cell phones of members and nonmembers. The messages invoke the name of a defunct credit union, Norlarco CU, which was acquired by Public Service CU in Denver (Coloradoan.com Dec. 1). The text messages say recipients' accounts have been restricted and they must call a toll free number. To unlock the account, they are instructed to enter their debit or credit card number, personal identification number (PIN) and expiration date.
Several members of Public Service CU received the message, according to its website. The credit union told members to not respond in any way to the message and to "Delete it immediately. It is a scam."
In Cheyenne, Wyoming, Warren FCU, members received a similar scam, prompting the Better Business Bureau serving Northern Colorado and Wyoming to tell the Coloradoan, "It seems like credit unions are specifically targeted."
In California, credit unions in Redwood City and Merced were targeted with the same kinds of messages. San Mateo CU, Redwood City, issued a press release saying it had not sent a text message received by consumers. In Merced, another credit union as well as customers of AT&T cell phone accounts were targeted, reported the sheriff's office (Merced Sun-Star Nov. 26).
Bridgeton, Mo.-based Vantage CU, which was been targeted before in previous waves of scams, said fraudsters started sending text-message phishing scams again to members and non-members last weekend in the credit union's name. Eric Acree, vice president, told the St. Louis Post-Dispatch that the credit union is trying to educate members about its security procedures so they don't fall for the fake messages. The credit union never contacts accountholders with an unsolicited text message, he told the newspaper.
In Nampa, Idaho, police said scammers sent text messages with an emergency notification about their accounts to consumers. Mountain Gem CU was targeted by the scammers, and Northwest Christian CU and IDADIV CU used their websites to warn consumers about the scam.
Wednesday, December 2, 2009
You Can Buy Used ATMs On Craigslist
After searching Craigslist for a seller, he found a bar owner looking to liquidate assets. He paid $750 for the ATM, and after a hacker friend looked over the accompanying manual, he was able to get 1,000 account numbers to print out.
ATM Skimmers Make Off With $70,000 in Chicago

Police are confirming media accounts of two ATM thieves which made off with $70,000 from a bank ATM after they attached a device to the machine to record card data and used a camera to record a card holder’s personal identification numbers as they punched them in.
The bank declined to comment on the theft other than to confirm that the Secret Service had been notified as well as the police. The Secret Service did not comment. Media reports said the two were caught on surveillance cameras placing the device and then returning to collect it and use the data to make the withdrawals.
See how the scam works: http://www.utexas.edu/police/alerts/atm_scam/
Tuesday, December 1, 2009
Friday, November 27, 2009
Christmas Carols Available From The Chins
Saturday, November 21, 2009
Buddy, Can You E-Mail Me 100 Bucks?
What if you could send money to that friend who loaned you $20 last week by using your mobile phone rather than having to go through the trouble of trekking to the ATM or mailing a check? All you'd need would be your buddy's e-mail address or cell number—and presto.
Folks in Japan and Europe can already do that. Soon Americans will, too. Studies show that U.S. consumers, particularly the younger set, have embraced the convenience of online shopping and e-banking and are now ready to move to the next frontier: person-to-person mobile payments. A recent poll by Mercatus, a financial consulting firm, showed that the proportion of people ages 26 to 34 who had used a cell phone to buy goods or pay for a product or service had doubled, to 14%, in the past year. "We are at the tipping point," says Mercatus managing partner Robert Hedges.
That's why a host of banks and financial companies are gearing up to add person-to-person payments to their existing mobile and online banking platforms.
[Read story at BusinessWeek.com/by Amy Feldman].
http://www.businessweek.com/magazine/content/09_47/b4156068763985.htm
Thursday, November 19, 2009
What if your Phone could read barcodes?
Check online prices for a DVD player.
Scan a book and check for reviews.
Scan the milk and add it to your grocery list.
I know what you’re thinking. That’s impossible, right? You heard the camera just wasn’t good enough.
Actually, it is good enough. But you can’t use just any old barcode technology. You need RedLaser – just maybe the most advanced 1D barcode recognition technology on planet earth.
Skeptical?
The future of shopping at: http://redlaser.com/
Bill Rogers spoke on similar technology and offered an outstanding video clip at the recent CU InfoTECH '09 Conference in Palm Springs. Bill said, "One attendee approached me after my presentation and said if he left the conference right now, that he already got his money worth and thanked me for a great program."
To book Bill and the future technology program, send an email to billrogers@swbell.net or call Bill at 1-800-745-2455.
Tuesday, November 17, 2009
Sick of Extension Cords?
Or, um, use an extension cord.
..
CUNA Technology Council presents best of show award
The award was presented at the Bank Administration Institute's Retail Delivery Conference Nov. 3-5 in Boston.
Saylent Technologies develops software solutions and services to increase non-interest income and core deposits. It won the Best of Show award for its Card360 solution, a portfolio optimization suite to help credit unions maximize the performance and satisfaction of their card programs.
Card360 is the engine behind CO-OP Financial Services' Revelation product, used by CO-OP's debit processing customers.
Since 2001, the CUNA Technology Council has presented the Best of Show award to the exhibitor that demonstrates a commitment to delivering technology that will further the growth of products and services in the credit union marketplace.
Thursday, November 12, 2009
Hilton Hotels Available Thru iTunes
 Offered gratis on iTunes, the Hilton Worldwide app could come in handy for stranded travelers thanks to a feature that lets you find hotels near you, by address or airport, and gives you directions from your current location.
Offered gratis on iTunes, the Hilton Worldwide app could come in handy for stranded travelers thanks to a feature that lets you find hotels near you, by address or airport, and gives you directions from your current location.The app will also let you choose bed and pillow type — plus if you don’t think you’ll have the strength to make a request once you get in, you can put your order for room service in via iPhone, too.
Sounds good, but it still has to compete with Priceline.com’s app (which boasts William Shatner as the icon) already iTunes’ fifth-most-downloaded free app after launching a week ago.
Fed will require bank customers and CU members to OK overdrafts
The rule, which comes as Congress is scrutinizing hefty overdraft fees, will take effect by July 1, 2010 for new customers and Aug. 15, 2010 for existing customers.
Consumers who want financial institutions to pay transactions that exceed their cash or credit limits can give their consent orally or in writing, Fed officials said Thursday.
More at: http://www.usatoday.com/money/industries/banking/2009-11-12-fed-overdraft-rule_N.htm
Wednesday, November 4, 2009
Shift Happens: Fall 2009 Version
http://www.flixxy.com/technology-and-media-convergence.htm
FBI warns consumers of increased phishing scam attempts
According to the FBI, potential victims of this type of fraud will receive a so-called "spear phishing" e-mail that contains an infected e-mail attachment or a link that sends the e-mail recipient to a website that is infected. Malware which contains a keylogger program is then installed on the victim's computer once they click on the link or attachment.
The keylogger is then used to track account information, and that information is used to steal from the victim via fund transfers or to create additional accounts in the victim's name.
The FBI has found that transferred funds of funds from the created accounts are then diverted into bank accounts of individuals that have been recruited to serve as payment processors through work-at-home advertisements or job search websites. The unwitting individuals then transfer the money that arrives in their accounts to overseas locales through a wire transfer service.
The FBI has advised customers that do their banking online to contact their financial institution to ensure that they are employing all the appropriate security and fraud prevention services their institution offers.
Tuesday, November 3, 2009
Data breach victims at 4 x greater fraud risk
Data breach notifications are intended to help consumers take protective action," said Mary Monahan, managing partner and research director at Javelin Strategy & Research, which conducted its third annual survey of nearly 5,000 U.S. consumers.
"Notification is critical because consumers are over four times more likely to encounter actual fraudulent transactions if they receive a data-breach notification," Monahan said in a press release. "But our research shows a disconnect between breach notifications and consumer awareness of risk, which results in individuals not being adequately protected."
During the past three years, roughly 11% of consumers received a breach notification, said the report. More than one-third of breach victims experienced exposure of their Social Security numbers, and 15% had their ATM personal identification numbers (PINs) compromised.
Despite almost 20% of breach victims suffering some kind of fraud in the past year, only 2% attribute their fraud to the breach.
Saturday, October 31, 2009
October News & Views Published Below
Friday, October 23, 2009
100 Dirtiest Sites to Avoid for Safety's Sake
The security vendor has compiled a list of this year's 100 "Dirtiest Websites." Just by visiting these sites, Web users could see their PCs infected with viruses or even have their sensitive personal data stolen by cyber criminals, even if they don't download or click on anything in particular.
Symantec said the average number of threats per malicious site is 23. However, all of the websites that made the top 100 list have on average 18,000 per site, with 40 percent having over 20,000 security threats. The company also said that three quarters of the sites have been distributing malware for over six months.
As expected just under half of the websites offered adult content, but what is more surprising is that other 52 websites covered a random selection of topics such as deer hunting, catering, figure skating, legal services and electronics.
"There has been exponential growth in the number of online threats that are constantly evolving as cybercriminals look for new ways to target your money, identity or assets. In 2008, most new infections occurred while people were surfing the web," said Marian Merritt, Symantec's internet safety advocate.
Thursday, October 22, 2009
Wife's First Hunting Trip
I couldn't believe it...the first time ever! I never thought he'd be
willing to share his 'guy time' with me. And being the thoughtful
man that he is, he even gave me an opening day present. He
calls it 'The First Timers Lucky Hat'. I'm so fortunate to be married
to him. I have attached a picture of me in my lucky hat.
Wednesday, October 21, 2009
Take a look at something technologically entertaining
In the game, which is created with Silverlight and runs in your browser, you play an IT pro (either Matt or Alicia) whose objective is to keep the network running smoothly while encountering a host of technical problems that are presented as games and puzzles, ranging from the absurd to things you might encounter in the real life of an IT pro. As you work through the tasks, you'll learn about and use Microsoft technologies to solve problems, encounter hidden Easter Eggs, earn geek points, and get to post your high scores for others to compete against.
75 interesting credit union name changes in 2009
From this year’s new names:
- 11 credit unions included the word “Community”: Arlington Community, Champion Community, Community, Community Driven, Memberfocus Commmunity, My Community, NMTW Community, Prestige Community, Total Community, Valley One Community and Vue Community.
- 7 reduced their names to acronyms: CEFCU, CSE, MaPS, MCT, ME/CU, NMTW and USE.
- 7 are coined names: Altana, Aventa, Cinfed, Genisys, Meritrust, TruStone and Vue Community.
- 3 use the number “one”: Alabama One, Metro 1 and Valley One Community.
- 3 credit unions ditched the word “First” in their name, while one put it in: University First.
- 2 credit unions used alphanumeric constructions: Med5 and Metro 1.
http://thefinancialbrand.com/2009/10/21/2009-cu-name-changes/
Tuesday, October 20, 2009
Email is Social, and it’s not Going Anywhere
Email is the original opt-in tactic, while social and mobile are newcomers. And email works in tandem with most other tactics to increase engagement, deliver relevant content and build contact databases.
Dispelling the Myth that Social Media is going to Abolish Email
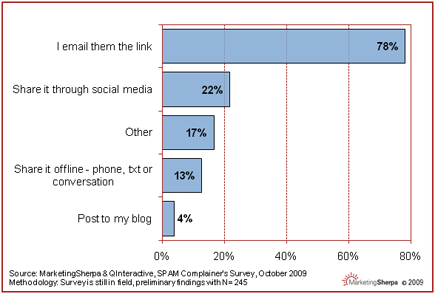
In the chart above, we take one view of how email is used to share information, because this activity is so central to social media sites. Email is dominant, even in this regard.
When we look at media use over the last 15 years, we see a pattern of aggregation and adoption rather than replacement. Some media suffer in the exchange, but none are eliminated entirely. More commonly, their uses become more refined.
For example, we may find that Twitter and Facebook gradually reduce our use of email to convey quick messages and content to social groups, but it’s far less likely that social media will replace email for commercial transactions, receipts and the like.
Pa. man charged with defrauding 3 CUs in ponzi scheme
Eugene D. Miley, 58, is accused of selling fictitious certificates of deposit (CDs) to Moonlight CU, Worthington; VANtage Trust CU, Wilkes-Barre; and Stanwood Area CU, New Stanton. Miley allegedly served as a financial broker for the credit unions, offering to locate and purchase various high interest rate CDs. Miley used the money he received from the credit unions for his personal use. He also generated fake statements about the purchase, interest rates and redemption information for the CDs.
"Miley claimed to be helping his clients earn a good return on their investments, but this was simply an illusion," said Attorney General Tom Corbett in a statement. "As with other ponzi schemes, the money received from new clients was used to pay off older investors, or siphoned off for personal use, until the flow of money stopped--causing the operation to collapse and leaving victims with nothing more than empty promises."
Miley is accused of selling $2.08 million in certificates between 2006 and 2008. He sold $1.3 million to Moonlight CU; $594,000 to VANtage Trust CU; and $99,000 to Stanwood Area CU, according to the attorney general's office.
Miley has been taken into custody and will appear for a preliminary hearing Nov. 20.
He will be charged with one count of securities fraud for creating a scheme to defraud, a second degree felony punishable by up to 10 years in prison and a $1 million fine; and one count of securities fraud for the sale of unregistered securities, a third-degree felony punishable by up to seven years in prison and a $250,000 fine.
Miley also will be charged with three counts each of theft by deception and theft by failure to make required disposition of funds--all third degree felonies, punishable by up to seven years in prison and $15,000 fines.
Miley is not licensed to operate as a financial investment company, financial adviser or financial products dealer. The funds for his fraudulent investments were funneled through PNC Bank accounts belonging to him and his business. The transactions were conducted using a PNC Bank branch in Cranberry Township, Pa., Corbett said.
Monday, October 12, 2009
Dade County FCU Deploys Anti-Fraud Tools
DCFCU is using the Aithent Case Management Solution to link all its fraud and compliance processes across its internal systems, enhancing both case management and the ability to produce compliant regulatory reports, the credit union said.
The credit union said benefits include easy access to information, reducing the need for redundant data entry and easing the burden on IT staff.
Aithent is a New York-based provider of information management solutions to financial, government and health care organizations.

Friday, October 9, 2009
FBI Phish Phry reels in 53 scam suspects
The Federal Bureau of Investigation (FBI) began arresting 53 individuals in the U.S. Wednesday on charges of conducting a vast financial fraud based on phishing or tricking Internet users into revealing their bank account information at two of the nation's largest banks--Bank of America and Wells Fargo.
Operation Phish Phry netted arrests in Southern California, Nevada and North Carolina, said the FBI. In addition, 47 co-conspirators in Egypt are being charged by authorities there.
This is the largest number of defendants ever charged in a cybercrime case, said the FBI in a press release. The group allegedly stole at least $2 million from 2007 through September 2009 from hundreds and perhaps thousands of the banks' customers.
Indictments in a U.S. District Court in Los Angeles accuse three California residents of masterminding the U.S. portion of the scam--Kenneth Joseph Lucas, 25; a friend, Jonathan Preston Clarke; and Nichole Michelle Merzi, Lucas' former girlfriend. They directed associates to recruit "runners" to set up bank accounts to receive funds stolen from the compromised accounts.
The online component of the scam initiated in Egypt, where defendants sent mass e-mail messages that appeared to come from the banks, said the FBI. Recipients who clicked on a link in the messages were sent to a fake website identical or similar to the banks' sites, where they were asked to enter information such as their account numbers, passwords, Social Security numbers and drivers' license numbers.
The U.S. group would transfer funds into their own accounts and remit money back to accomplices in Egypt.
Each of the 53 defendants named in the indictment is charged with conspiracy to commit bank fraud and wire fraud, which carries a maximum penalty of 20 years in prison. Various defendants also are charged with bank fraud; aggravated identity theft; conspiracy to commit computer fraud, specifically unauthorized access to protected computers in connection with fraudulent bank transfers; and domestic and international money laundering.
Some analysts said the arrests won't have much impact on the number of online banking scams that have hit businesses, including credit unions. Many other groups are involved in similar fraudulent phish schemes, they said (The New York Times Oct. 8).
Thursday, October 8, 2009
Vantage CU uses Twitter for account transfers
Released Sept. 28, tweetMyMoney is free to Vantage members. It allows them to monitor their account balances, deposits, withdrawals, holds and cleared checks. Members also can transfer funds within their accounts. The program can be accessed from a computer or mobile phone.
About 70 members have enrolled. They access the program by enrolling in Vantage's online banking program and setting up a Twitter account. Members also must sign up to "follow" Vantage on Twitter. tweetMyMoney works through Twitter's Direct Message function--which allows users to send messages to each other privately. In this case, members send messages to Vantage.
The program "utilizes a set of codes that you send via direct message to the credit union and get information back," Eric Acree, executive vice president of operations, told News Now.
(Read the rest of the story at: http://www.cuna.org/newsnow/09/system100709-7.html?ref=hed)
Tuesday, October 6, 2009
Scams hit four CUs
The following scams have been reported:
Suffolk FCU, Medford, N.Y., and Island FCU, Hauppauge, N.Y., debit card holders were targets of scam text or voice messages, which tell members their debit card numbers have been deactivated, police said. The victims were instructed to call a phone number to provide account and personal identification numbers to reactivate their accounts. Police reminded the public that credit unions do not contact members by mail, phone or Internet to request account information (Newsday Oct. 3).
Shoreline CU, Two Rivers, Wis., reports that a website--www.SurveyLot.com--is mailing fraudulent cashier's checks to Internet visitors nationwide, according to Sharon Tome, Shoreline chief operating officer. The checks are written for $3,975.20 and contain the routing number for the credit union and an account number--now closed--of a Shoreline member. The credit union has returned roughly $30,000 worth of checks that tried to clear through the account, Tome said. No Shoreline members have been victimized by the scam, she added. Shoreline officials are alerting other financial institutions that the checks are fraudulent (Herald Times Reporter Oct. 1).
Paducah (Ky.) FCU, has received dozens of calls from members who received a suspicious text message that said in part: "This is an automated message from Paducah FCU. Your ATM card has been suspended. To reactivate, call URGENT at 1-866-571-7629." When the number was dialed, the caller heard an automated message requesting the caller's bank account number. The telephone number has been disconnected, and the credit union is not aware of any members who were victimized by the scam (INFED Oct. 1).
Thursday, October 1, 2009
CU Tech Conference Highlights the Fall Season; Coming November 9-12, 2009
Register by Oct. 9 and save $50 per registration.
http://cuconferences.com/tech09/TECH09_Agenda.htm
September News & Views Published Below

Wednesday, September 30, 2009
Bank sends email to wrong Gmail account: Who's at fault?
Account information sent to wrong Gmail address
According to various news reports and the court filing, a customer of Rocky Mountain Bank in Wyoming asked a bank employee to email loan statements to a third-party representative. Unfortunately, the bank employee sent the information to the wrong Gmail address. To make matters worse, the data file attached to the erroneously-sent email contained confidential information on 1,325 accounts of other customers. The file included names, addresses, tax identification numbers, and loan information.
After discovering the mistake, Rocky Mountain Bank personnel tried to recall the email, without success. They also sent a follow-up message to the recipient, instructing them to delete the message and attachment without opening it and requesting that he or she contact the bank to discuss their actions. The bank also contacted Google to determine if the account was active or dormant, and what could be done to prevent the data from being disclosed.
Google declined to provide any information about the Gmail account in question without a court order. Rocky Mountain Bank filed suit to force the disclosure of account information and asked the Court to seal the case. On September 18, 2009, a federal judge denied the bank’s request to seal the case.
(For the rest of the story: http://blogs.techrepublic.com.com/itdojo/?p=1031&tag=nl.e099.dl090930&tag=nl.e099 )
Wednesday, September 23, 2009
Red Bluff woman prevails in bank protest
The bank executive verbally agreed to cut her rate from 30 percent to 12.99 percent, where it was in January before it was increased, Minch said.
Upset that the bank had raised her interest rate, the 46-year-old Red Bluff resident vented her outrage Sept. 8 on YouTube, vowing to stop making payments on the card. The video has received more than 230,000 Web hits.
Minch broke news of the deal Saturday on YouTube in a video titled "Debtors Update: Bank of America Responds!!!" The six-minute clip had generated about 1,000 views by Monday afternoon.
Minch said she was contacted by Bank of America's Jeff Crawford, who asked why she produced the first video. "He was very polite," Minch said on YouTube. "He didn't make any demands about pulling down the YouTube video."
Initially, Crawford offered to drop the rate to 16.99 percent. But he reconsidered after Minch told him Bank of America has been allowed to borrow money virtually interest-free from the federal government.
(Read the rest of the story at: http://www.redding.com/news/2009/sep/22/red-bluff-woman-prevails-in-bank-protest/)
GPS Could Lead to Home Invasion
 When the victims got home, they found that their house had been ransacked and just about everything worth anything had been stolen.The thieves had used the GPS to guide them to the house. They then used the garage remote control to open the garage door and gain entry to the house.
When the victims got home, they found that their house had been ransacked and just about everything worth anything had been stolen.The thieves had used the GPS to guide them to the house. They then used the garage remote control to open the garage door and gain entry to the house.The thieves knew the owners were at the football game, they knew what time the game was scheduled to finish and so they knew how much time they had to clean out the house. It would appear that they had brought a truck to empty the house of its contents.
Something to consider if you have a GPS - don't put your home address in it. Put a nearby address (like a store or gas station) so you can still find your way home if you need to, but no one else would know where you live if your GP S were stolen.
Tuesday, September 22, 2009
FBI report: Most bank robbers get away with it
Of the $61.6 million in cash stolen, only about 19 percent - $8.9 million - was recovered.
Although the report does not reveal the arrest rate, it does show that just 3,342 of the 8,393 crooks known to be involved in the robberies were identified. Of those identified, 43 percent were determined to be narcotics users and 19 percent had previously been convicted of a bank-related crime.
The South saw the most robberies - 2,100 - followed by the West, with 1,857.
Banks in metropolitan areas claimed the highest number of heists - 3,388 - with small cities or towns following, with 2,189.
In all, bank-related crime in 2008 was slightly below that reported in 2007. [Read story at Scripps Howard News/by Lisa Hoffman].
Monday, September 21, 2009
Thursday, September 17, 2009
How do I use Prey to help recover a stolen laptop?
The information collected includes:
> Status of the computer
> List of running programs and active connections
> Detailed network and WI-FI report
> Screenshot of running desktop
> A picture of the thief (if the stolen laptop is equipped with a Webcam)
Of course you are probably thinking this is a lot of information to be sending out, especially since, with this setup, your laptop will be sending out this information even when the laptop isn’t stolen. Ah, but the creators have thought of that as well.

You can configure Prey to only send out the information if it finds a certain Web URL that you created in the event of the laptop being stolen. We’ll address that in a bit. First, let’s look at how to get the program and install it.
Read more about Prey at: http://blogs.techrepublic.com.com/window-on-windows/?p=1543&tag=nl.e064
Wednesday, September 16, 2009
Internet Criminals Stepping Up Attacks
 About 87% of data breaches could be thwarted with simple-to-intermediate preventive measures, said a Department of Homeland Security official.
About 87% of data breaches could be thwarted with simple-to-intermediate preventive measures, said a Department of Homeland Security official. Friday, September 11, 2009
Open Solutions Takes Two-Factor to Teller Line
 Using the Veri-Fast solution, members swipe their ATM/debit card, enter their PIN number and once verified, the software instantly retrieves the relationship profile.
Using the Veri-Fast solution, members swipe their ATM/debit card, enter their PIN number and once verified, the software instantly retrieves the relationship profile.The company said that in addition to reducing fraud, Veri-Fast boosts service and efficiencies by automating the retrieval of accountholder files and eliminating teller keystrokes.
Veri-Fast is being offered to financial institutions that run on The Complete Credit Union and The Complete Banking Solution core applications and can be customized to integrate with other core platforms, the company said.
Wednesday, September 9, 2009
FCU Embezzler Went More Than Four Years Without Discovery
Melissa Laliberte, former bookkeeper and convicted embezzler for the now defunct Meriden Franco American Federal Credit Union, went more than four years before anyone realized the extent of her theft.
According to court documents and NCUA records, Laliberte embezzled almost $744,000 from the credit union between January 2004 and July of 2008, when the NCUA closed the institution. At the time of the its closure, Meriden Franco-American had almost $338,000 in assets, suggesting that Lalibert had embezzled more than twice the credit union's assets.
According to court papers filed in the case, Lalibert diverted member's cash deposits for her own use, made checks out payable to herself or her own creditors and made direct cash withdrawals from the CU. She also failed to note withdrawals from her own accounts and those of her husband and presented false reports to the CU's board of directors, according to the documents.
The legal filings also revealed that, as the extent of the embezzlement grew, Lalibert succeeded in convincing five other CUs to invest a total of $400,000 in certificates of deposit with the CU. This infusion of cash enabled her to keep the embezzlement going past the time it would have otherwise been discovered, the documents said.
Saturday, September 5, 2009
Friday, September 4, 2009
Coming: Wearable Device That Enables Interactions With The World of Data
Pranav Mistry is the genius behind Sixth Sense, a wearable device that enables new interactions between the real world and the world of data.
http://www.ted.com/talks/pattie_maes_demos_the_sixth_sense.html
Wednesday, September 2, 2009
100 Years of Inspiration - 26 Films That Changed the World of Visual Effects
http://www.flixxy.com/movies-visual-effects.htm
August News & Views Published Below

Tuesday, September 1, 2009
CU Tech Conference Highlights the Fall Season; Coming November 9-12, 2009
(Click on photo to enlarge)
 You can learn how to enjoy operational efficiency and profitability in the pre-conference workshop on Monday, November 9. Then join in the conference program on Tuesday and Wednesday which includes:
You can learn how to enjoy operational efficiency and profitability in the pre-conference workshop on Monday, November 9. Then join in the conference program on Tuesday and Wednesday which includes:> Future Technology and Your Credit Union
> Next Generation Risks> Leveraging Technology and Attracting New Members
> Reinventing Information Technology
> An inside Look at Mobile Banking
> Identity Theft and Where We're At Today
> Web Application Firewalls
> The Art and Science of LoanAcquisition
The legendary Riveria Resort & Spa in Palm Springs, CA creates an inspiring atmosphere for CU InfoTech '09. Click on the above photo for a great look at the Riveria.For a brochure on the entire program, click here: http://cuconferences.com/tech09/09%20InfoTech%20FINAL.pdf
Wednesday, August 26, 2009
NCUA Warns of Phony Fraud Alert
 The letter, which purports to be a fraud alert, has so far been received by one federal credit union. It is numbered “09-FCU-09” and deals with phishing scams.
The letter, which purports to be a fraud alert, has so far been received by one federal credit union. It is numbered “09-FCU-09” and deals with phishing scams.The agency urges people not to run the compact discs because it could corrupt security.
Credit unions receiving this package or a similar package should contact your NCUA Regional Office or the NCUA Fraud Hotline at 1-800-827-9650.
Monday, August 24, 2009
Credit Unions Receive Fraud Buster Awards
Recipients of the Fraud Buster Awards are recognized for protecting their credit unions, their members and members of other credit unions from fraud. Credit unions stopped fraud at every touch point in the system, said FSCC.
"The award recipients demonstrated their commitment and diligence in preventing fraud for members nationwide. It is not just their members who would be impacted, but also members of other credit unions," said Sarah Canepa Bang, FSCC president/CEO.
Financial institutions and businesses lose more than $48 billion annually from fraudulent activities, according to the Federal Trade Commission.
"Fraud is one of the most expensive security challenges facing credit unions today. And as a (credit union service organization), it is our duty to provide tools that support prevention and training for credit unions," added Bang.
FSCC's Operation Advisory Committee of stockholder credit unions reviews activity and looks at ways to prevent and detect fraud through rule changes, products and services. The committee organized the awards program in 2000.
In eight years, credit unions have stopped more than $7.4 million in attempted fraud, said FSCC.
Wednesday, August 19, 2009
It's OK to Write Passwords on Post-it Notes . . . Providing! The Perfect 4-Character Password

I noticed their password was "MickeyMinnieGoofyPluto" and asked why it was so long."Because," my son explained, "they say it has to have at least four characters."
Tuesday, August 18, 2009
Stopwatch Measures How Long It Takes to Load a Web Page
 The StopWatch can only measure websites that can be displayed in a frame. Some websites use javascript to break out of frames. This is not a StopWatch bug.
The StopWatch can only measure websites that can be displayed in a frame. Some websites use javascript to break out of frames. This is not a StopWatch bug.Click here to check your credit unions website: http://www.numion.com/Stopwatch/index.html
Monday, August 17, 2009
Man gives teller ID before robbing Credit Union
The FBI says Jarell Paul Arnold of Anchorage is being held on federal bank robbery charges.
The FBI alleges Arnold walked into an Alaska USA Federal Credit Union branch Friday and inquired about the balance on his account. The teller asked for his name, account number and ID.
Authorities say he complied, and then handed over a receipt with a note on the back that said he had a gun and demanded money. The FBI says he got away with about $600. Authorities arrested Arnold on Monday. Duh!
Court records say Arnold was sentenced to 57 months in prison for bank robbery in 2004.
ATM Problems: Mouse Rolls in the Dough
According to press reports, an employee at the Gem Stop Chevron in La Grande was surprised to find a mouse inside the ATM, happily nesting on a bed of shredded $20 bills.
 The ATM continued to function despite the mouse, employees said. The mouse had chewed up two bills and damaged another 14 to make his nest, but the deployer reinserted all the money that wasn't extensively damaged.
The ATM continued to function despite the mouse, employees said. The mouse had chewed up two bills and damaged another 14 to make his nest, but the deployer reinserted all the money that wasn't extensively damaged.The deployer released the mouse and employees could not answer questions about how the mouse got inside the machine.
Sunday, August 16, 2009
Scammers try to horn in on 'clunkers' program
WASHINGTON (8/14/09)--The Credit Union National Association (CUNA) is warning credit unions to educate their members about scammers seeking to take advantage of the recently renewed Cash for Clunkers program. The Better Business Bureau (BBB) has reported that identity thieves are using the program to skim sensitive information from consumers.
The National Highway Traffic Safety Administration, prior to the passage of the Cash for Clunkers legislation earlier this year, reported websites that were soliciting for the names, addresses and Social Security numbers of potential customers, said BBB.
Consumers also reportedly have been solicited by companies that offer to help fill out the paperwork needed to receive vouchers to take part in the program.
The BBB has informed potential program participants that they do not need to register or receive a voucher to participate in the Cash for Clunkers program. Also, auto dealerships, not individuals, are responsible for filling out any paperwork associated with the program.
The program, which gives car buyers up to $4,500 for trading in older, gas-guzzling vehicles for more fuel-efficient cars, was responsible for an estimated 250,000 new car sales in July.
The BBB recommends that interested participants consult the official government site for the program, cars.gov, to answer any questions they may have.
Thursday, August 6, 2009
When it Comes to Business: Common Sense VS. Nonsense
… John Ruskin (1819-1900)
Wednesday, August 5, 2009
Fraud report: Call center fraud is evolving
Cybercriminals are infiltrating the call center, with scams evolving into a new criminal professional call service that can spoof any number in the U.S. and offer cash out in multiple languages.
 According to RSA Anti-Fraud Command Center's monthly Online Fraud Report for June, the service enables phone numbers to be customized depending on the state where the account holder resides. It also enables fraudsters to accept incoming calls, posing as the genuine account holder.
According to RSA Anti-Fraud Command Center's monthly Online Fraud Report for June, the service enables phone numbers to be customized depending on the state where the account holder resides. It also enables fraudsters to accept incoming calls, posing as the genuine account holder."Service providers in the underground have evolved phone fraud services into a singular location to provide other fraudsters with the ability to conduct phone channel fraud to any destination and in any language," the report said.
The service helps the cybercriminals to increase their profits while significantly lowering the risk of exposure, said RSA.
Other findings for June:
> More than 13,000 phishing attacks were identified, a 10% increase from May and the highest in 11 months;
> Attacks against credit union brands remained constant--at 18%, the same as in May. After peaking at 38% of attacks in February, attacks against credit unions dropped to 22% in March and 14% in April.
> Attacks against regional bank brands increased 60% while national brand attacks dropped more than 50%; and
> Fast-flux attacks, the denial of service using sophisticated networks of computers called botnets, increased by 5% to make up 56% of the hosting methods of attacks. Hijacked websites accounted for 26% of the attack methods.
Sunday, August 2, 2009
July News & Views Published Below
 CU SECURITY & TECHNOLOGY News - Providing a brief summary of news and information related to security and technology issues for credit unions - Plus some interesting and fun web sites . . .
CU SECURITY & TECHNOLOGY News - Providing a brief summary of news and information related to security and technology issues for credit unions - Plus some interesting and fun web sites . . .Thursday, July 30, 2009
CUSO Preps XCalibur Testing for October Using Biometric ID
The XCalibur card was created by CUSO XCard Systems LLC with assistance from IBM Global Engineering Solutions. One of the features that sets it apart from typical debit and credit cards is a biometric touch sensor that authenticates the user before activation. The card can then only be activated by the user or an authorized user, according to XCard. Certain key functions allow the user to pick which account they want to use for a particular transaction, according to the CUSO.
In October, 50 cards will tested, said Vic Pantea, president/CEO of Member Gateways LLC, a product development CUSO that has been involved in the card’s pilot. A simultaneous testing for Visa and MasterCard standards will also take place. From these tests, any final revisions will be made and the card device will enter final production.
CU*Answers is providing card processing and core system testing and Beyond Marketing LLC will market the card. Kent Displays Inc. created the screen display and Seidenfaden Design came up with the prototype sleeve. Prevas Engineering has also played a role in the overall development.
Employees and board members at three credit unions will be among the first to test the XCalibur card, a biometric card that can function as a single debit, gift and loyalty card.
The XCalibur card was created by CUSO XCard Systems LLC with assistance from IBM Global Engineering Solutions. One of the features that sets it apart from typical debit and credit cards is a biometric touch sensor that authenticates the user before activation. The card can then only be activated by the user or an authorized user, according to XCard. Certain key functions allow the user to pick which account they want to use for a particular transaction, according to the CUSO.
In October, 50 cards will tested, said Vic Pantea, president/CEO of Member Gateways LLC, a product development CUSO that has been involved in the card’s pilot. A simultaneous testing for Visa and MasterCard standards will also take place. From these tests, any final revisions will be made and the card device will enter final production.
CU*Answers is providing card processing and core system testing and Beyond Marketing LLC will market the card. Kent Displays Inc. created the screen display and Seidenfaden Design came up with the prototype sleeve. Prevas Engineering has also played a role in the overall development.
Wednesday, July 29, 2009
You Said What? 43 Things Actually Said in Job Interviews
Believe it or not, the above statements weren't overheard in bars or random conversations -- they were said in job interviews.
Maybe you were nervous, you thought the employer would appreciate your honesty, or maybe you just have no boundaries. Whatever the reason, you can be certain that you shouldn't tell an interviewer that it's probably best if he doesn't do a background check on you. (And yes, the hiring manager remembered you said that.)
 We asked hiring managers to share the craziest things they've heard from applicants in an interview. Some are laugh-out-loud hysterical, others are jaw-dropping -- the majority are both. They will relieve anyone who has ever said something unfortunate at a job interview -- and simply amuse the rest of you.
We asked hiring managers to share the craziest things they've heard from applicants in an interview. Some are laugh-out-loud hysterical, others are jaw-dropping -- the majority are both. They will relieve anyone who has ever said something unfortunate at a job interview -- and simply amuse the rest of you.Hiring managers shared these 43 memorable interview responses:
Why did you leave your last job?"I have a problem with authority." - Carrie Rocha, chief operating officer, HousingLink
Tell us about a problem you had with a co-worker and how you resolved it"The resolution was we were both fired." - Jason Shindler, CEO, Curvine Web Solutions
What kind of computer software have you used?"Computers? Are those the black boxes that sit on the floor next to the desks? My boss has one of those. He uses it. I don't have one. He just gives me my schedule and I follow it." - Greg Szymanski, director of human resources, Geonerco Management Inc.
What are your hobbies and interests?"[He said] 'Well, as you can see, I'm a young, virile man and I'm single -- if you ladies know what I'm saying.' Then he looked at one of the fair-haired board members and said, 'I particularly like blondes.'" - Petri R.J. Darby, president, darbyDarnit Public Relations
Why should we hire you?"I would be a great asset to the events team because I party all the time." - Bill McGowan, founder, Clarity Media Group
Do you have any questions?"Cross-dressing isn't a problem is it?" - Barry Maher, Barry Maher & Associates
"If you were a fruit, what fruit would you be?" - Megan Garnett, Articulate Leadership Team, Articulate Communications Inc.
"What do you want me to do if I cannot walk to work if it's raining? Can you pick me up?" - Christine Pechstein, career coach
"I was a chamber of commerce executive once hiring a secretary. [The candidate asked] 'What does a chamber of commerce do?'" - Mary Kurek, Mary Kurek Inc. Visibility Consulting
Hey, there's a lot more of these at: http://tinyurl.com/lmhfdt or
http://bit.ly/1h7uhM
CU robber goes to confession, returns money
 Police do not know the name of the man who went to a Walnut Creek, Calif., church Sunday night and told the priest during confession that he had robbed the Walnut Creek branch of Patelco CU Thursday afternoon. He left the church after giving the priest $1,200 he said he had robbed from the credit union (Contra Costa Times July 28).
Police do not know the name of the man who went to a Walnut Creek, Calif., church Sunday night and told the priest during confession that he had robbed the Walnut Creek branch of Patelco CU Thursday afternoon. He left the church after giving the priest $1,200 he said he had robbed from the credit union (Contra Costa Times July 28).After the man left, the priest called the police.
"I don't know if that was the entire amount or a percentage of the amount," Shelly James, Walnut Creek police lieutenant, told the newspaper. "He said he felt remorse."
After handing the Patelco teller a note Thursday, the man claimed he had a gun. Police will arrest the robber when he is found.
Tuesday, July 28, 2009
Fraudulent checks circulating with CU's name
Fraudulent checks bearing the Meadville (Pa.) Area FCU name and a distorted logo are being mailed to various individuals nationwide.
The check is made payable to the individual in the amount of $2,950.00 with a date of July 9. The item is printed on burgundy check stock and at first glance may appear valid. However, a closer look reveals that MidAtlantic is misspelled and other items are placed in the wrong locations on the face of the check.
The checks are accompanied by a letter from Greenwater Mystery Shopping. The recipient is asked to complete certain tasks within 48 hours. A request to call its office is listed first. Then, the recipient is asked to go to a local Sears or Wal-Mart and send a money gram to someone in Canada.
Meadville Area FCU is gathering evidence to assist the U.S. Postal Investigators in their pursuit of the perpetrators. Anyone with relevant information should contact the credit union.
Saturday, July 25, 2009
Delta Begins In-Flight Wi-Fi Rollout (and It's Free Until Next Year)
 The service, provided by Aircell, will be $9.95 on flights less than three hours and $12.95 for anything longer. These short flights will all fit into the former category, just the beginning of the system-wide roll-out that Delta wants to put in place next year.
The service, provided by Aircell, will be $9.95 on flights less than three hours and $12.95 for anything longer. These short flights will all fit into the former category, just the beginning of the system-wide roll-out that Delta wants to put in place next year.However, that expansion will be dealt an early blow next year as Delta replaces many of those shuttle flights with contract carriers that don't offer such fancy features. In other words, we're still not quite to the point where mid-air surfing is standard fare, but we're getting close.
Thursday, July 23, 2009
More Advertisers Turning to Internet, Relying Less On Printing
 At the same time, less than half are using radio advertising (46%), television advertising (46%) and mobile advertising (39%). The Harris poll found there is a regional difference as advertisers in the South are more likely to use radio advertising (57%) and television advertising (56%) while those in the West are least likely to use both (39% each).
At the same time, less than half are using radio advertising (46%), television advertising (46%) and mobile advertising (39%). The Harris poll found there is a regional difference as advertisers in the South are more likely to use radio advertising (57%) and television advertising (56%) while those in the West are least likely to use both (39% each).Among those advertisers who are using each of these types of media, there is a difference in the level of usage since last year. Three-quarters of those who use Internet advertising (74%) say they are incorporating it more often while 69 percent of those who use mobile advertising are using it more often compared to a year ago.
Unsurprisingly, the largest drop is with print advertising as half (49%) of those who use it are using it less often compared to a year ago while 41 percent are using it the same amount.
Of those who use Internet advertising just 14 percent say they use it in a standalone campaign, while 54 percent say the use it in an integrated campaign with other media and 33 percent use Internet advertising in both types of campaigns equally.

















