The Credit Union InfoSecurity Conference, the original and premier conference dedicated solely to credit union security, is holding its next summit on June 5-7, 2013 at the Platinum Hotel and Spa in Las Vegas.
Register for the event
The conference, which features industry leaders in their respective fields sharing their firsthand knowledge and practical advice on securing credit unions, is an incredible opportunity to gain new insight, network with credit union peers, and browse the Security Vendor Reception.
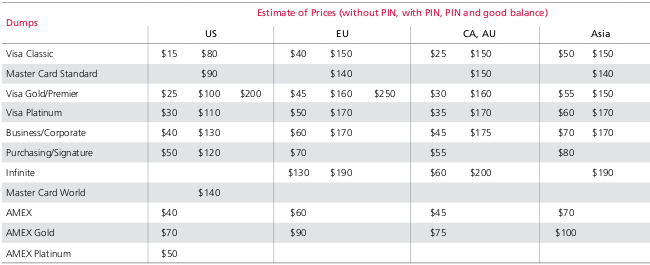
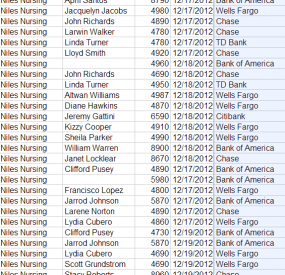
Possible topics to be covered at the upcoming summit include mobile security, data forensics, insider threats, incident response, social engineering, secure cloud storage, virtual desktop security, and fighting banking fraud.
If you are interested in attending the event, be sure to register
here (https://www.cunews.com/infosecurity-conference.html).