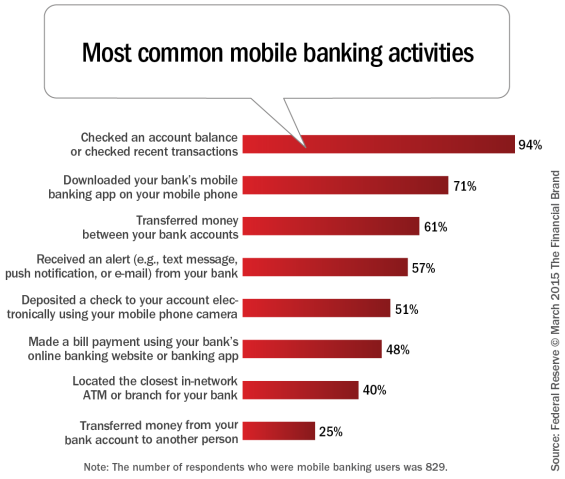
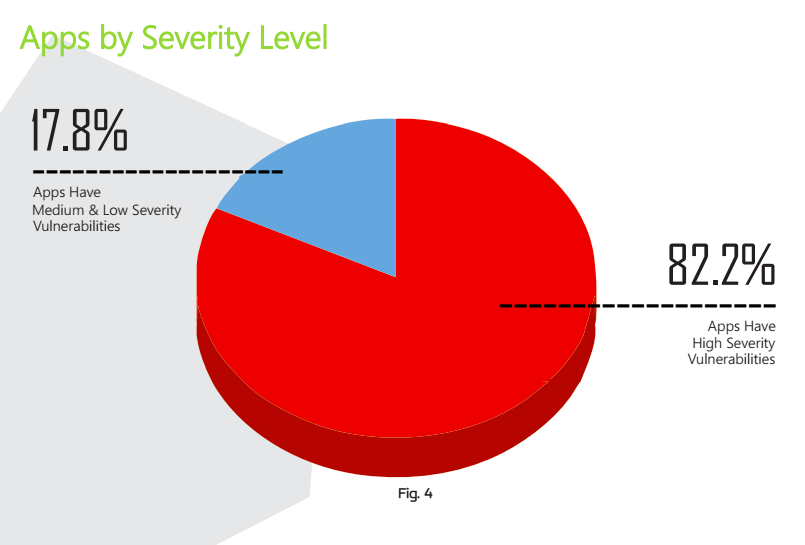
Saying it was an inventive solution to a "massive problem," judges at the RSA Conference's Innovation Sandbox, today, awarded the title of Most Innovative Company to Waratek, creator of a runtime application self-protection solution for Java.
In addition to Waratek, the finalists included BugCrowd, Cybereason, Fortscale, NexDefense, SecurityDo, SentinelOne, TrustInSoft, Vectra, and Ticto, which was named runner-up. The judges have never named a runner-up in the Sandbox's 10-year history, but apparently the fight between Waratek and Ticto was so close, that the judges deemed it necessary.
Read the full article.