 |
| Image source: Article |
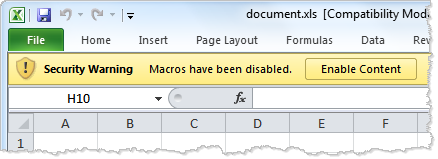
Intruders use the above techniques to execute code in Microsoft Office documents to compromise the system.
Read the article to learn more about the techniques.
A site dedicated to providing credit unions with relevant news and information related to security and information technology.
 |
| Image source: Article |
No comments:
Post a Comment