We've launched a new site and would love to see you there!
Friday, June 26, 2015
Saturday, June 6, 2015
After hacking, government workers warned of potential fraud
An immense hack of millions of government personnel files is being treated as the work of foreign spies who could use the information to fake their way into more-secure computers and plunder U.S. secrets.
The breach was an embarrassing showing for the U.S. government’s vaunted computer-defense system for civilian agencies — dubbed “Einstein” — which is costing $376 million this year alone.
Read the full article.
 |
| Image Source: Article |
Read the full article.
Labels:
computer-defense system,
cyberattack,
data breach,
Einstein,
hack
Friday, June 5, 2015
Massive data breach could affect every federal agency
China-based hackers are suspected once again of breaking into U.S. government computer networks, and the entire federal workforce could be at risk this time.
The Department of Homeland Security said in a statement that data from the Office of Personnel Management — the human resources department for the federal government — and the Interior Department had been compromised.
Read the full article.
 |
| Image Source: Article |
Read the full article.
Labels:
data breach,
federal workforce,
hackers,
intrusion detection
Thursday, June 4, 2015
FBI issues warning to retailers of credit card malware
FBI has issued a warning that criminal hackers are using new malicious software to steal personal financial data.
Bureau cyber investigators have identified software signatures used in a new point-of-sale malware dubbed ‘Punkey’.
Read the full article.
 |
| Image Source: Google Images |
Read the full article.
Tuesday, June 2, 2015
THE MASHUP OF BRICKS AND PIXELS
Consumers are melding technology and reality. What does this mean for credit unions?
Like other consumers, credit union members get through each day with the assistance of digital and mobile technologies.
Read the full article.
| Image Source: Article |
Read the full article.
Labels:
bricks and clicks,
mobile technologies,
self-service
Monday, June 1, 2015
Tipping the Data Breach Odds in Your Favor
Catastrophic data breaches are becoming the new norm.
Each week, new data breaches surface, making it clear that cyber criminals are getting the upper hand in breaking into networks and stealing assets.
Read the full article.
 |
| Image Source: Article |
Read the full article.
PCI: 5 New Security Requirements
Five best practices noted in version 3.0 of the PCI Data Security Standard will become requirements after June 30, and smaller merchants are likely to be the most affected, says one security expert.
The PCI Security Standards Council says merchants of all sizes are increasingly at risk, and that these requirements reflect areas all businesses should address.
Read the full article.
 |
| Image Source: Article |
Read the full article.
Friday, May 29, 2015
5 things you should know about cyber insurance
The right coverage can help soften the blow of a data breach. But don't expect to be bailed out if your security plan is flawed.
So when CEO Michael Lynton disclosed in a media interview earlier this year that Sony's intrusion-related costs would be almost entirely paid for by insurers, the news renewed attention on the topic of cyber insurance in a major way.
Read the full article.
 |
| Image Source: Article |
Read the full article.
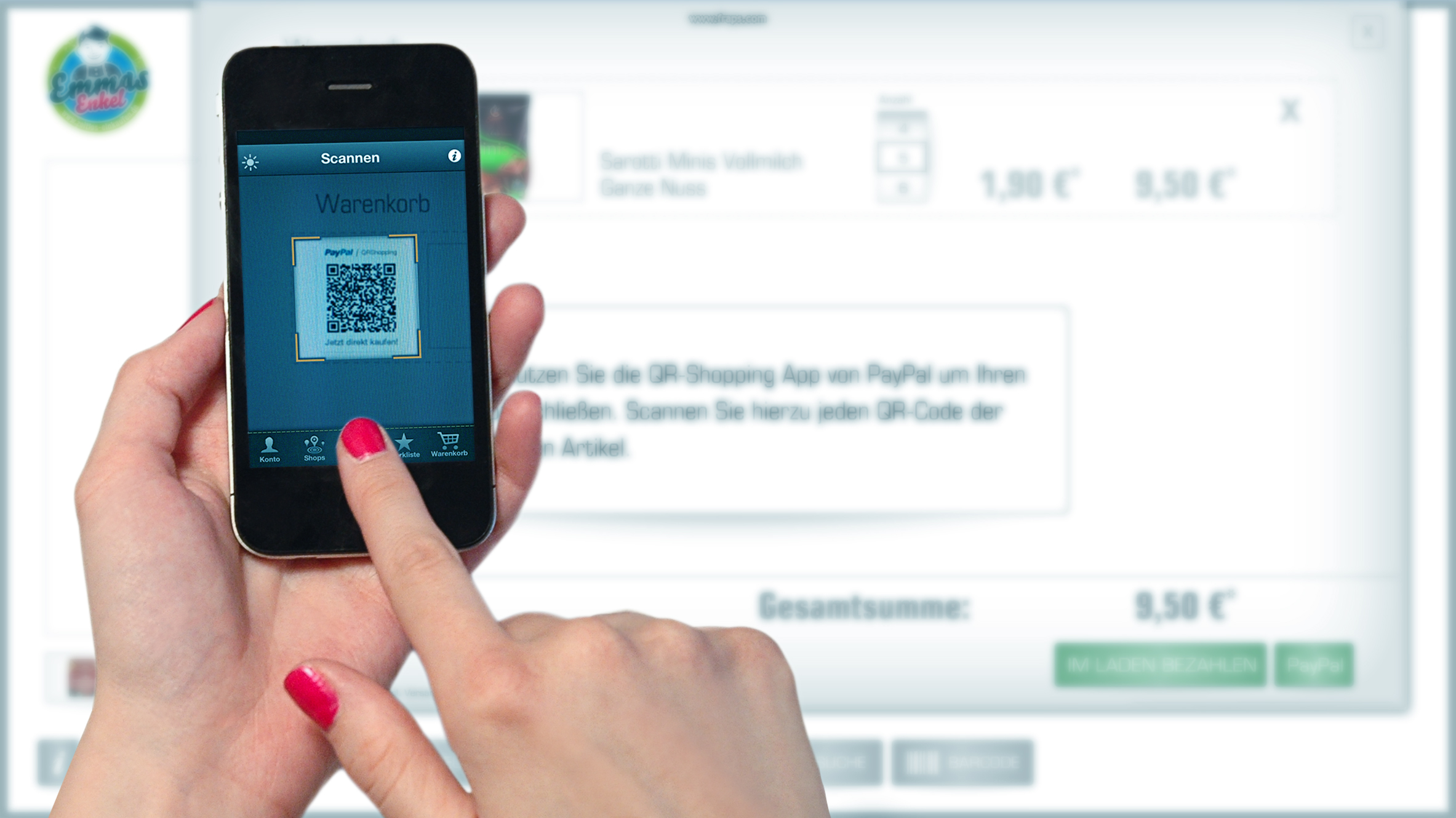
Filene: Community, technology transforming payments
A new white paper from the Filene Research Institute explores the monumental shift taking place in the way consumers exchange money, and the implications for credit unions.
“At the heart of this change is the evolution of payments and financial services based on disruptive innovations in commerce at the intersection of key macro trends that include mobile, retail, marketing services, data and technology."
Read the full article.
 |
| Image Source: Google Images |
Read the full article.
The insider threat
An interesting shift in mindset was on display at the recent RSA Security Conference in San Francisco. People have stopped focusing on perimeter security – which is essentially the act of stopping the bad guys from getting into your systems.
Almost every commentator was delivering the same mantra: Perimeter security is no longer enough.
Read the full article.
 |
| Image Source: Article |
Read the full article.
Thursday, May 28, 2015
Rising data breach costs show need for national merchant standards
The average costs for businesses related to data breaches are going up, another sign of the need for Congress to adopt NAFCU-supported national data security merchants and retailers.
According to the “Cost of Data Breach Study: Global Analysis,” released Wednesday by the Ponemon Institute, the average consolidated total cost of a data breach is $3.8 million, up 23 percent since 2013.
Read the full article.
 |
| Image Source: Article |
Read the full article.
Mary Meeker's stunning 2015 presentation on the state of the web
Every year, Mary Meeker of Kleiner Perkins Caufield & Byers puts together a massive presentation about the state of the web.
In the report, she usually nails the biggest trends happening in digital as well as identifying the most important up-and-coming startups.
Read the full article.
 |
| Image Source: Article |
Read the full article.
Wednesday, May 27, 2015
6 Deadly Data Breach Prevention Sins
Cybercrime has become a worldwide issue, thanks to the growing sophistication of online techniques.
According to cybersecurity experts, there is no single fix – except for the awareness that cybercriminals continue to change their tactics and seek out the weakest defenses to compromise systems, and steal data and money.
Read the full article.
 |
| Image Source: Article |
Read the full article.
Labels:
cybercrime,
cybersecurity,
Data Breach Prevention
Tuesday, May 26, 2015
Is A Smart Office Right For Your Branch?
In today’s branching environment, credit unions are looking to better technology to help them improve member service, increase efficiency, and reduce costs.
Smart offices allow members to complete account and loan applications with representatives via video conferencing and other technological connections.
Read the full article.
 |
| Image Source: Article |
Read the full article.
Friday, May 22, 2015
Guardtime Announces BLT, New Blockchain Standard for Digital Identity
Guardtime, the first and only platform for ensuring the integrity of data and systems at industrial scale, today announced BLT, the authentication and signature protocol meant to replace RSA as the standard for digital identity.
In contrast to RSA’s reliance on quantum-vulnerable asymmetric key cryptography, BLT is based on Guardtime’s quantum-secure Keyless Signature Infrastructure (KSI) technology, which uses only hash function cryptography.
Read the full article.
 |
| Image Source: Google Images |
Read the full article.
Massive Clinton-era Internet bug shows pitfalls of Obama's 'backdoor' proposal
This week, computer researchers announced they found a massive weakness in Internet software. "Logjam," as they called it, allows hackers to spy on your online communications.
Logging into your email, bank or Facebook (FB, Tech30) on public Wi-Fi or over a virtual private network (VPN) isn't safe.
Read the full article.
 |
| Image Source: Article |
Read the full article.
Thursday, May 21, 2015
Cyber attacks a growing threat for US financial system
Online attacks by ever-skillful hackers are a growing threat to the stability of the US financial system, according to a report by a top-level government panel released Tuesday.
The 2015 report by the Financial Stability Oversight Council said that although US banks and financial businesses have been leaders in erecting barriers to hackers, cyber attacks still present a potential systemic danger.
Read the full article.
 |
| Image Source: Article |
Read the full article.
Financial Firms ‘Take Up To Three Months’ To Detect Cybersecurity Threats
Companies are putting themselves at significant risk of being hit by damaging cyber-attacks by not being able to detect advanced threats quickly enough, a report has claimed.
A study by the Ponemon Institute and sponsored by security firm Arbor Networks found that the ‘dwell time’ (the time taken for businesses to realise the possible threat) can be as much as several months, meaning they are not able to prepare and protect themselves adequately.
Read the full article.
 |
| Image Source: Article |
Read the full article.
Labels:
cyber-attacks,
Cybersecurity Threats,
dwell time
Wednesday, May 20, 2015
Business continuity and disaster recovery planning: The basics
Disaster recovery and business continuity planning are processes that help organizations prepare for disruptive events—whether those events might include a hurricane or simply a power outage caused by a backhoe in the parking lot.
The CSO's involvement in this process can range from overseeing the plan, to providing input and support, to putting the plan into action during an emergency.
Read the full article.
 |
| Image Source: Google Images |
Read the full article.
Can Financial Services Use Social Media Right?
Did you know a tenth of HSBC’s workforce is in compliance?
Meanwhile, similar trends are being seen in the U.S. and around the world.
The regulatory clampdown is happening at the same time that technology is transforming our world.
Read the full article.
 |
| Image Source: Article |
Read the full article.
The Art of (Cyber) War: Cybersecurity Tactics for All Financial Institutions
As financial institutions of every type and size -- national, regional and community banks, thrifts, mutuaIs, credit unions, and non-bank lenders -- increase their collection of personal information about their customers and employees, they become larger targets for a data privacy incident.
Financial institutions are truly in a cyber war and must fight this battle on four fronts: external threats, intentional misappropriation by rogue employees, data accidentally lost or misplaced, and vendor negligence; accordingly, proper tactics and strategy are essential for survival.
Read the full article.
 |
| Image Source: Google Images |
Read the full article.
Labels:
cybersecurity,
hacking,
Malware attacks,
Ramsomware
Saturday, May 16, 2015
Five tips to comply with the new PCI requirements
At the end of June, merchants that accept payment cards have five new security requirements to comply with -- and significant fines and other costs if they don't.
The new rules are part of the new Payment Card Industry Data Security Standard.
Read the full article.
 |
| Image Source: Article |
Read the full article.
Wednesday, May 13, 2015
Banks Eye IoT And Wearable Tech Apps
Banks and other transaction-focused companies are increasing their efforts to bring apps to the Apple Watch and other wearable technology – with an eye on creating a seamless shopping, payment and even budgeting experience for consumers via the Internet.
Driven in part by the Internet of Things trend, Royal Bank of Canada and MasterCard are working with Bionym, maker of a wristband that authenticates consumers via biometrics, according to American Banker.
Read the full article.
 |
| Image source: Article |
Read the full article.
Labels:
apple watch,
banking transactions,
biometrics,
internet of things,
jot,
mobile apps,
mobile payments
Tuesday, May 12, 2015
Cyberattacks Target Mobile Banking
Reports of 2.2 billion malicious attacks on computers and mobile devices in 2015’s first quarter and an evolving Dyre Wolf malware threat are reminders of the continuing need for financial institutions to remain vigilant.
In an epic quarter, Moscow-based security firm Kaspersky Lab released the “IT Threat Evolution Report for Q1 of 2015.”
Read the full article.
 |
| Image Source: Article |
Read the full article.
Labels:
cyberattacks,
IT Threat,
Kaspersky Lab,
mobile banking
When is a breach detection system better than an IDS or NGFW?
How would you describe the difference between a breach-detection system and a traditional intrusion detection/prevention system or next-generation firewall, particularly from the perspective of how each type of device interacts with network traffic?
In which enterprise settings would a breach-detection system be more appropriate to leverage?
Read the full article.
 |
| Image Source: Article |
Read the full article.
CU InfoSecurity Conference 2015 in Las Vegas
The Credit Union InfoSecurity Conference, the original and premier conference dedicated solely to credit union security, is holding its next summit on June 3-5, 2015 at the Golden Nugget Hotel & Casino in the heart of Fremont Street in Las Vegas.
Register for the event
The conference, which features industry leaders in their respective fields sharing their firsthand knowledge and practical advice on securing credit unions, is an incredible opportunity to gain new insight, network with credit union peers, and browse the Security Vendor Reception.
Possible topics to be covered at the upcoming summit include ransomware, active defense, cloud security, data encryption, breach prevention, pervasive security, device configuration, social media compliance, virtual branch security, virtual machine security, account takeover prevention, network security strategies, and cyber security intelligence.
If you are interested in attending the event, be sure to register here (https://www.cunews.com/infosecurity-conference.html).
Register for the event
 |
| Image source: CU News |
Possible topics to be covered at the upcoming summit include ransomware, active defense, cloud security, data encryption, breach prevention, pervasive security, device configuration, social media compliance, virtual branch security, virtual machine security, account takeover prevention, network security strategies, and cyber security intelligence.
If you are interested in attending the event, be sure to register here (https://www.cunews.com/infosecurity-conference.html).
Labels:
account takeover,
breach prevention,
cloud security,
credit union security,
cyber security intelligence,
encryption,
network security,
ransomware,
virtual branch security,
virtual machine security
Monday, May 11, 2015
MasterCard Speaks on Importance of Biometrics
MasterCard has been speaking about its digital securitization efforts at this year’s Risk to Reward conference in London, according to a Business Reporter article by Joanne Frearson. To that end, the company says it’s developing fingerprint and facial biometric systems.
It has also been working on its own biometric credit cards, which have already been tested in a pilot project in Norway and are slated to further expand their presence.
Read the full article.
 |
| Image source: Article |
Read the full article.
Friday, May 8, 2015
Credit Unions Seek Better AML Technology: Celent
A new report from Boston-based research firm Celent looked at how continuously evolving regulations, coupled with recent instances of money laundering rule violations, have led to the need for better technology in managing AML operations.
In the report titled, “Emerging Solutions in Anti-Money Laundering Technology,” Celent discussed a number of innovative solutions in the AML/Know Your Customer (KYC) space. Faced with pressures from growing compliance requirements and the need to cut costs, financial institutions are seeking technology that increases efficiency and frees up resources, Celent said.
Read the full article.
 |
| Image source: Article |
Read the full article.
Thursday, May 7, 2015
LA Suit Accuses Wells Fargo Of Misusing Consumer Data
The City of Los Angeles is suing Wells Fargo, alleging some bank employees in the state have been pressured to adopt “unfair, unlawful and fraudulent conduct” against customers, including but not limited to misusing confidential data.
In a civil suit filed Monday (May 4), L.A. City Attorney Mike Feuer claimed that Wells Fargo opened unauthorized accounts in customers’ names, refused to close those accounts even after those customers complained, and even “raided” client accounts for funds to open new accounts – all in an effort to meet sales quotas.
Read the full article.
 |
| Image source: Article |
Read the full article.
Wednesday, May 6, 2015
HR Answers: Prevent internal fraud
For credit unions nationwide, internal fraud represents a significant and growing problem.
The financial services sector has the highest incidence of internal fraud across 23 industries, according to the Association of Certified Fraud Examiners’ 2012 Global Fraud Survey: about 17 percent of all insider fraud incidents, vs. just over 10 percent each for government/public administration and manufacturing.
Read the full article.
 |
| Image Source: Article |
Read the full article.
Chip Card Shift Projected To Be Nearly Done By 2017
As the Oct. 1 deadline for the EMV merchant-liability shift inches closer, there’s going to be a lot more reports about which type of merchants are ready, and which aren’t.
There’s also going to be plenty of reports on which issuers have their credit and debit cards EMV-chip enabled (and which are behind).
Read the full article.
 |
| Image source: Article |
Read the full article.
THE BANKING INDUSTRY'S BIGGEST MOBILE CHALLENGE? MESSAGING
In recent years, the American Bankers Association (ABA) has emphasized that mobile banking is a major growth area for its industry.
The challenge, though, may be the messaging, not the technology.
Read the full article.
 |
| Image Source: Article |
Read the full article.
Tuesday, May 5, 2015
Anti-sandbox capabilities found in Dyre malware
A new version of Dyre malware, which recently reemerged to plague financial institutions in the form of the Dyre Wolf campaign, is now employing anti-sandbox techniques to avoid security professionals and pose a more insidious threat to financial enterprises.
New research from cloud-based security firm Seculert revealed that Dyre is capable of bypassing sandboxes by checking the system for processor cores. If only one core is found, Dyre terminates instantly.
Read the full article.
 |
| Image Source: Article |
Read the full article.
Stop Sending Me Threat Intelligence in Email
I’ve been talking to many different organizations recently about their sources of threat intelligence, and one thing I’ve heard numerous times is that some of the most timely, valuable threat intelligence they are receiving is via email.
I’ve even heard that we’ve made some progress with STIX, as sometimes STIX content is attached to the emails—poor TAXII must feel so left out.
Read the full article.
 |
| Image Source: Article |
Read the full article.
Banks and Credit Unions Decide Whether to Support Wearables
The official inauguration of Apple Watch brings great expectations inclusive of changing the way we think about how to gather data and turn it into information. Until now, achieving information gathering meant entering information via keyboard, voice or video.
More and more, bank and credit union customers prefer to bank wherever they are, using their smartphones, tablets or wearables as the remote control for their financial management. If consumers are using mobile-connected devices to streamline their to-dos, then what is next for these tiny, mobile computers?
Read the full article.
 |
| Image source: Article |
Read the full article.
Monday, May 4, 2015
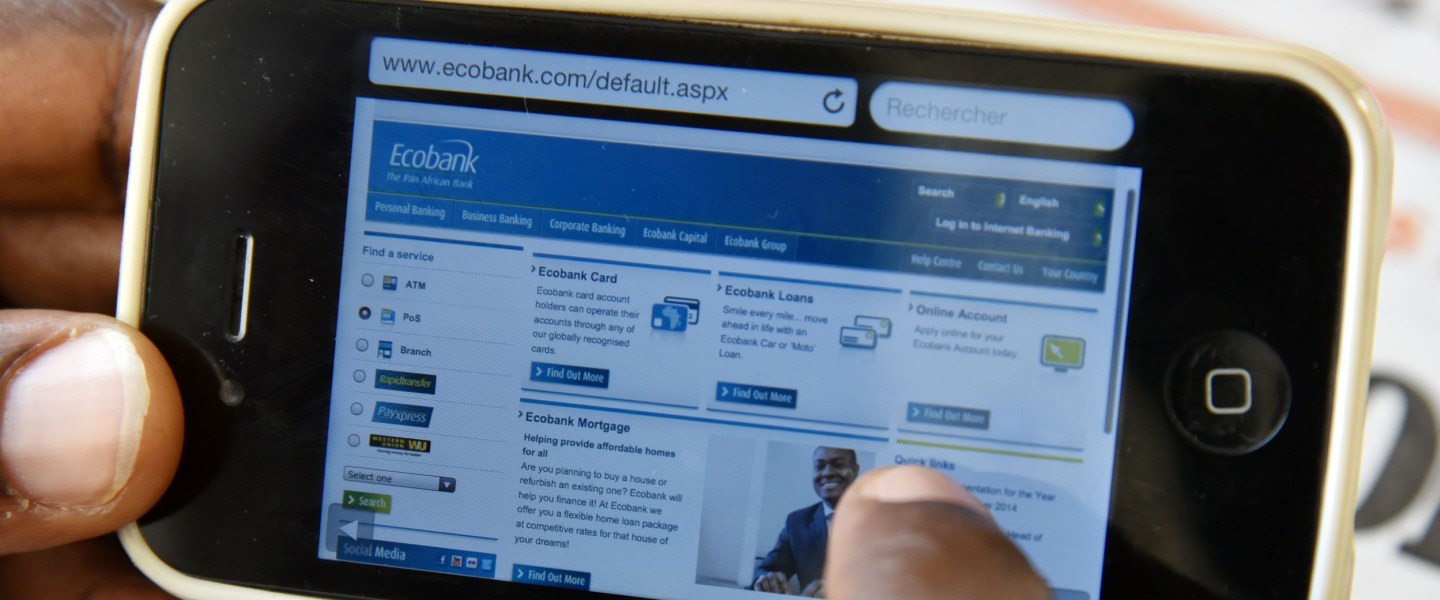
Why Has Mobile Banking Growth Stalled? Blame Hackers
After several years of dramatic growth, the adoption rate for mobile banking in the U.S. has slowed dramatically. Those who like to bank this way are doing it more often, but the industry is struggling to get more customers to go mobile.
A recent report from the Federal Reserve (Consumers and Mobile Financial Services 2015) found that 52 percent of smartphone owners with a bank account did at least one mobile banking transaction last year. That's not much of an increase from the 51 percent reported in 2013.
Read the full article.
 |
| Image source: Article |
Read the full article.
New payment systems put consumer data at risk: Ponemon
With new payment systems comes more risk to consumer data, a new survey indicates.
About 68% of payment-systems professionals say pressure to migrate to new payment systems puts customer data at greater risk instead of making it safer, according to a new survey by Experian and the Ponemon Institute.
Read the full article.
 |
| Image Source: Google Images |
Read the full article.
Takeaways From the 2015 Verizon Data Breach Investigations Report
Verizon’s annual Data Breach Investigations Report (DBIR), published since 2008, has become one of the most anticipated information security industry reports.
Think of it as the Data Breach Bible, as it dissects thousands of confirmed data breaches and security incidents from around the globe into emergent and shifting trends, providing us with insightful guidance to apply to our own security practices.
This year’s publication compiled the data of nearly 80,000 security incidents and more than 2,000 data compromises from 61 countries. The contributions from dozens of forensic firms, service providers, government agencies and international Computer Security Information Response Teams (CSIRT) help provide detailed findings based on 2014 incident and breach data.
Some of the items presented include:
Read the full article.
This post brought to you by: Read the full article.
Read the full article.
 |
| Image Source: Article |
This year’s publication compiled the data of nearly 80,000 security incidents and more than 2,000 data compromises from 61 countries. The contributions from dozens of forensic firms, service providers, government agencies and international Computer Security Information Response Teams (CSIRT) help provide detailed findings based on 2014 incident and breach data.
Some of the items presented include:
- Victim Demographics
- Breach Trends
- Indicators of Compromise
- Phishing
- Vulnerabilities
- and more...
Read the full article.
This post brought to you by:
 Read the full article.
Read the full article.
Labels:
data breach,
Data Breach Investigations Report,
data loss,
DBIR,
security incidents,
Verizon
Saturday, May 2, 2015
Three Keys to a Successful Cybersecurity Defense Program
Normally, the bait used to get the attention of senior accounting and finance members were topics like, “Trends to Fund Your Next Acquisition,” “Key Tax Strategies for the New Millennium,” “How to Attract and Retain High Performing Teams,” etc.
However, recently, I’ve noticed a new topic cropping up about this new business risk of “protecting your data” and “cybersecurity defense.”
Read the full article.
 |
| Image Source: Article |
Read the full article.
Friday, May 1, 2015
Forrester estimates that broad EMV chip adoption is half a decade away
Forrester Research predicts that “broad adoption” of plastic EMV chip-and-signature and chip-and-PIN payments in the U.S. will take several years, despite the looming fraud liability shift taking effect in October.
In a new report (PDF)published this week, called “Prioritize Tokenization to Secure the Payment Chain,” co-authors Andras Cser, Ed Ferrara and John Kindervag, said that widespread EMV adoption wouldn't occur until 2020.
Read the full article.
 |
| Image Source: Article |
Read the full article.
Labels:
EMV chip and PIN,
encryption,
PCI-DSS,
Tokenization
Thursday, April 30, 2015
Regulator Sets New Rules on Credit-Union Membership
The chief regulator of U.S. credit unions passed a new rule designed to curtail how some in the industry gather new members, a move credit unions say is too tough and rival banks say is too weak.
The National Credit Union Administration, the regulator for the more than 4,000 federally chartered credit unions, on Thursday approved final rules that prohibit credit unions from setting up charities and other associations designed solely to attract customers who otherwise wouldn’t be eligible for membership.
Read the full article.
 |
| Image source: Article |
Read the full article.
Payment Innovation Outpacing Security: Study
Security hasn’t kept pace with technology and there is widespread concern that new payment technology such as virtual currencies, mobile payments and e-wallets increase a breach risk, according to a new study.
The study found that emerging payments technologies coming in the wake of 2014’s mega retail breaches are threatening a landscape in which financial institutions, retailers, payment processors and credit card brands are facing more scrutiny than ever before.
Read the full article.
 |
| Image source: Article |
Read the full article.
Credit Unions May Partner With Bitcoin Exchanges to Offer Competitive Products
Credit unions may consider partnering with Bitcoin exchanges such as Coinbase if they are to continue offering competitive international payments services to their customers.
In the report titled Understanding Bitcoin’s Implications for Credit Union Services, the group touches upon the two grave concerns stemming the rise of Bitcoin, High Volatility and Security. Should the digital currency’s volatility reduce to generally acceptable levels and the security of private keys is ensured, credit unions may replace their core functions with Bitcoin.
Read the full article.
 |
| Image source: Article |
Read the full article.
Labels:
american express,
bitcoin,
coinbase,
credit card,
MasterCard,
Visa
The Opportunity (In New Members, Revenue) For CUs In Mobile Wallets
In financial services, nobody builds personal relationships like credit unions can—and nobody understands your credit union’s members better than you do.
More and more members want to connect with their credit union through the mobile channel.
Read the full article.
 |
| Image source: Article |
Read the full article.
Next Frontier for Mobile Payments: Adding Loyalty Programs
Even as credit unions are figuring out the emerging space that is mobile payments, there already are glimpses of the next frontier — adding loyalty programs to mobile.
For years the concept of loyalty was simple: consumers used their credit and debit cards to make purchases and earned rewards by doing so. With the advent of mobile payments, however, suddenly the picture becomes much murkier.
Read the full article.
 |
| Image source: Article |
Read the full article.
Labels:
credit card,
debit cards,
loyalty programs,
mobile payments
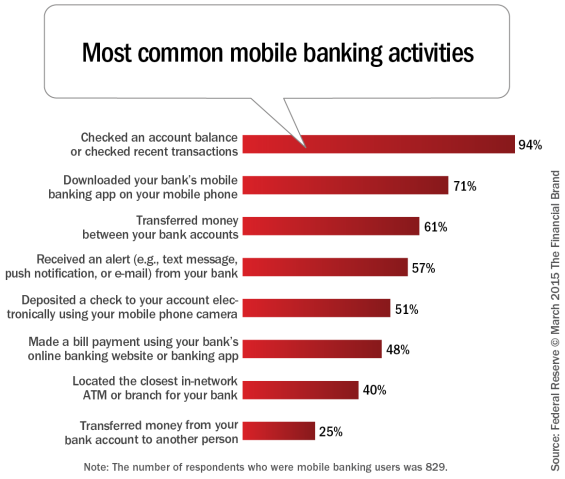
Design Is The New Differentiator In Mobile Banking
As understanding of basic mobile banking applications increases and the differentiation between mobile banking apps becomes less defined, the importance of mobile design takes center stage. The key is to combine functionality with simplicity.
A study from the Federal Reserve shows that there are untapped markets waiting for mobile banking. Millions of consumers are going to start banking on mobile in the next twelve months. But millions more aren’t interested.
Read the full article.
 |
| Image source: Article |
Read the full article.
Labels:
financial applications,
mobile apps,
mobile banking,
mobile innovation,
ui,
user experience,
ux
Wednesday, April 29, 2015
Self-Service Payment Revolution Keeps ATMs Relevant
The fact that ATM fee hikes still cause controversy shows consumers still demand ATMs, even in an era when payments and other transactions seems to be moving to a mobile platform.
It is the self-service component of mobile and other digital payment and financial transaction technology that is actually contributing to ATMs' health.
Read the full article.
 |
| Image source: Article |
Read the full article.
How Banks and Credit Unions Protect Your Personal Information
From regularly changing passwords to safeguarding credit card numbers, there’s no shortage of ways to protect yourself from hackers who are dead set on stealing your personal information. What may be less familiar, though, are the measures that financial institutions take to protect this data.
Hackers can be relentless and difficult to stop. But that doesn’t mean financial institutions aren’t doing what they can to thwart them, or that the government hasn’t recognized the severity of the threat.
Read the full article.
 |
| Image source: Article |
Read the full article.
Subscribe to:
Posts (Atom)






