A $170,000 cyberheist last month against an Illinois nursing home provider starkly illustrates how large financial institutions are being leveraged to target security weaknesses at small to regional banks and credit unions.
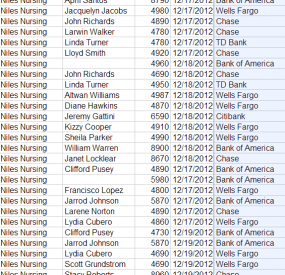
The attack on Niles Nursing Inc. provides a textbook example. On Monday, Dec. 17, 2012, computer crooks logged into the company’s online banking accounts using the controller’s credentials and tunneling their connection through his hacked PC.
At the beginning of the heist, the miscreants added 11 money mules to Niles’ payroll, sending them automated clearing house (ACH) payments totaling more than $58,000, asking each mule to withdraw their transfers in cash and wire the money to individuals in Ukraine and Russia.
In total, the attackers appear to have recruited at least two dozen money mules to help haul the stolen loot.
Read the article to learn more.