We've launched a new site and would love to see you there!
Friday, June 26, 2015
Saturday, June 6, 2015
After hacking, government workers warned of potential fraud
An immense hack of millions of government personnel files is being treated as the work of foreign spies who could use the information to fake their way into more-secure computers and plunder U.S. secrets.
The breach was an embarrassing showing for the U.S. government’s vaunted computer-defense system for civilian agencies — dubbed “Einstein” — which is costing $376 million this year alone.
Read the full article.
| Image Source: Article |
Read the full article.
Labels:
computer-defense system,
cyberattack,
data breach,
Einstein,
hack
Friday, June 5, 2015
Massive data breach could affect every federal agency
China-based hackers are suspected once again of breaking into U.S. government computer networks, and the entire federal workforce could be at risk this time.
The Department of Homeland Security said in a statement that data from the Office of Personnel Management — the human resources department for the federal government — and the Interior Department had been compromised.
Read the full article.
| Image Source: Article |
Read the full article.
Labels:
data breach,
federal workforce,
hackers,
intrusion detection
Thursday, June 4, 2015
FBI issues warning to retailers of credit card malware
FBI has issued a warning that criminal hackers are using new malicious software to steal personal financial data.
Bureau cyber investigators have identified software signatures used in a new point-of-sale malware dubbed ‘Punkey’.
Read the full article.
| Image Source: Google Images |
Read the full article.
Tuesday, June 2, 2015
THE MASHUP OF BRICKS AND PIXELS
Consumers are melding technology and reality. What does this mean for credit unions?
Like other consumers, credit union members get through each day with the assistance of digital and mobile technologies.
Read the full article.
| Image Source: Article |
Read the full article.
Labels:
bricks and clicks,
mobile technologies,
self-service
Monday, June 1, 2015
Tipping the Data Breach Odds in Your Favor
Catastrophic data breaches are becoming the new norm.
Each week, new data breaches surface, making it clear that cyber criminals are getting the upper hand in breaking into networks and stealing assets.
Read the full article.
| Image Source: Article |
Read the full article.
PCI: 5 New Security Requirements
Five best practices noted in version 3.0 of the PCI Data Security Standard will become requirements after June 30, and smaller merchants are likely to be the most affected, says one security expert.
The PCI Security Standards Council says merchants of all sizes are increasingly at risk, and that these requirements reflect areas all businesses should address.
Read the full article.
| Image Source: Article |
Read the full article.
Friday, May 29, 2015
5 things you should know about cyber insurance
The right coverage can help soften the blow of a data breach. But don't expect to be bailed out if your security plan is flawed.
So when CEO Michael Lynton disclosed in a media interview earlier this year that Sony's intrusion-related costs would be almost entirely paid for by insurers, the news renewed attention on the topic of cyber insurance in a major way.
Read the full article.
| Image Source: Article |
Read the full article.
Filene: Community, technology transforming payments
A new white paper from the Filene Research Institute explores the monumental shift taking place in the way consumers exchange money, and the implications for credit unions.
“At the heart of this change is the evolution of payments and financial services based on disruptive innovations in commerce at the intersection of key macro trends that include mobile, retail, marketing services, data and technology."
Read the full article.
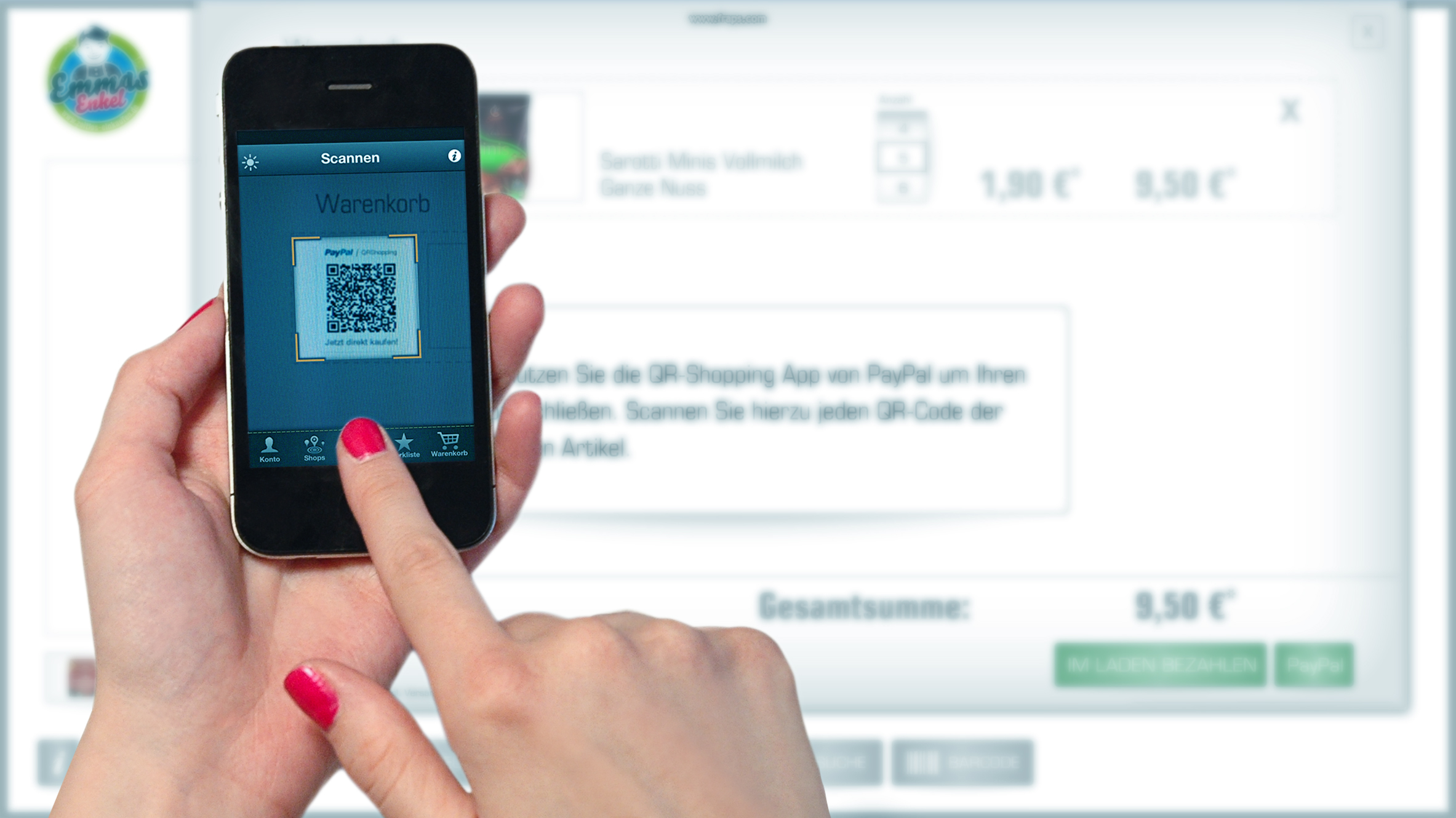 |
| Image Source: Google Images |
Read the full article.
The insider threat
An interesting shift in mindset was on display at the recent RSA Security Conference in San Francisco. People have stopped focusing on perimeter security – which is essentially the act of stopping the bad guys from getting into your systems.
Almost every commentator was delivering the same mantra: Perimeter security is no longer enough.
Read the full article.
| Image Source: Article |
Read the full article.
Thursday, May 28, 2015
Rising data breach costs show need for national merchant standards
The average costs for businesses related to data breaches are going up, another sign of the need for Congress to adopt NAFCU-supported national data security merchants and retailers.
According to the “Cost of Data Breach Study: Global Analysis,” released Wednesday by the Ponemon Institute, the average consolidated total cost of a data breach is $3.8 million, up 23 percent since 2013.
Read the full article.
| Image Source: Article |
Read the full article.
Mary Meeker's stunning 2015 presentation on the state of the web
Every year, Mary Meeker of Kleiner Perkins Caufield & Byers puts together a massive presentation about the state of the web.
In the report, she usually nails the biggest trends happening in digital as well as identifying the most important up-and-coming startups.
Read the full article.
| Image Source: Article |
Read the full article.
Wednesday, May 27, 2015
6 Deadly Data Breach Prevention Sins
Cybercrime has become a worldwide issue, thanks to the growing sophistication of online techniques.
According to cybersecurity experts, there is no single fix – except for the awareness that cybercriminals continue to change their tactics and seek out the weakest defenses to compromise systems, and steal data and money.
Read the full article.
| Image Source: Article |
Read the full article.
Labels:
cybercrime,
cybersecurity,
Data Breach Prevention
Tuesday, May 26, 2015
Is A Smart Office Right For Your Branch?
In today’s branching environment, credit unions are looking to better technology to help them improve member service, increase efficiency, and reduce costs.
Smart offices allow members to complete account and loan applications with representatives via video conferencing and other technological connections.
Read the full article.
| Image Source: Article |
Read the full article.
Friday, May 22, 2015
Guardtime Announces BLT, New Blockchain Standard for Digital Identity
Guardtime, the first and only platform for ensuring the integrity of data and systems at industrial scale, today announced BLT, the authentication and signature protocol meant to replace RSA as the standard for digital identity.
In contrast to RSA’s reliance on quantum-vulnerable asymmetric key cryptography, BLT is based on Guardtime’s quantum-secure Keyless Signature Infrastructure (KSI) technology, which uses only hash function cryptography.
Read the full article.
| Image Source: Google Images |
Read the full article.
Labels:
authentication,
blockchain,
BLT,
digital identity,
Keyless Signature Infrastructure,
signature protocol
Massive Clinton-era Internet bug shows pitfalls of Obama's 'backdoor' proposal
This week, computer researchers announced they found a massive weakness in Internet software. "Logjam," as they called it, allows hackers to spy on your online communications.
Logging into your email, bank or Facebook (FB, Tech30) on public Wi-Fi or over a virtual private network (VPN) isn't safe.
Read the full article.
| Image Source: Article |
Read the full article.
Thursday, May 21, 2015
Cyber attacks a growing threat for US financial system
Online attacks by ever-skillful hackers are a growing threat to the stability of the US financial system, according to a report by a top-level government panel released Tuesday.
The 2015 report by the Financial Stability Oversight Council said that although US banks and financial businesses have been leaders in erecting barriers to hackers, cyber attacks still present a potential systemic danger.
Read the full article.
| Image Source: Article |
Read the full article.
Financial Firms ‘Take Up To Three Months’ To Detect Cybersecurity Threats
Companies are putting themselves at significant risk of being hit by damaging cyber-attacks by not being able to detect advanced threats quickly enough, a report has claimed.
A study by the Ponemon Institute and sponsored by security firm Arbor Networks found that the ‘dwell time’ (the time taken for businesses to realise the possible threat) can be as much as several months, meaning they are not able to prepare and protect themselves adequately.
Read the full article.
| Image Source: Article |
Read the full article.
Labels:
cyber-attacks,
Cybersecurity Threats,
dwell time
Wednesday, May 20, 2015
Business continuity and disaster recovery planning: The basics
Disaster recovery and business continuity planning are processes that help organizations prepare for disruptive events—whether those events might include a hurricane or simply a power outage caused by a backhoe in the parking lot.
The CSO's involvement in this process can range from overseeing the plan, to providing input and support, to putting the plan into action during an emergency.
Read the full article.
| Image Source: Google Images |
Read the full article.
Can Financial Services Use Social Media Right?
Did you know a tenth of HSBC’s workforce is in compliance?
Meanwhile, similar trends are being seen in the U.S. and around the world.
The regulatory clampdown is happening at the same time that technology is transforming our world.
Read the full article.
| Image Source: Article |
Read the full article.
The Art of (Cyber) War: Cybersecurity Tactics for All Financial Institutions
As financial institutions of every type and size -- national, regional and community banks, thrifts, mutuaIs, credit unions, and non-bank lenders -- increase their collection of personal information about their customers and employees, they become larger targets for a data privacy incident.
Financial institutions are truly in a cyber war and must fight this battle on four fronts: external threats, intentional misappropriation by rogue employees, data accidentally lost or misplaced, and vendor negligence; accordingly, proper tactics and strategy are essential for survival.
Read the full article.
 |
| Image Source: Google Images |
Read the full article.
Labels:
cybersecurity,
hacking,
Malware attacks,
Ramsomware
Saturday, May 16, 2015
Five tips to comply with the new PCI requirements
At the end of June, merchants that accept payment cards have five new security requirements to comply with -- and significant fines and other costs if they don't.
The new rules are part of the new Payment Card Industry Data Security Standard.
Read the full article.
| Image Source: Article |
Read the full article.
Wednesday, May 13, 2015
Banks Eye IoT And Wearable Tech Apps
Banks and other transaction-focused companies are increasing their efforts to bring apps to the Apple Watch and other wearable technology – with an eye on creating a seamless shopping, payment and even budgeting experience for consumers via the Internet.
Driven in part by the Internet of Things trend, Royal Bank of Canada and MasterCard are working with Bionym, maker of a wristband that authenticates consumers via biometrics, according to American Banker.
Read the full article.
| Image source: Article |
Read the full article.
Labels:
apple watch,
banking transactions,
biometrics,
internet of things,
jot,
mobile apps,
mobile payments
Subscribe to:
Comments (Atom)



